Governance & Risk Management , Incident & Breach Response , Managed Detection & Response (MDR)
Lumin PDF Leak Exposed Data on 24 Million Users
Data on Users of PDF Editing Tool Found in Accessible Database
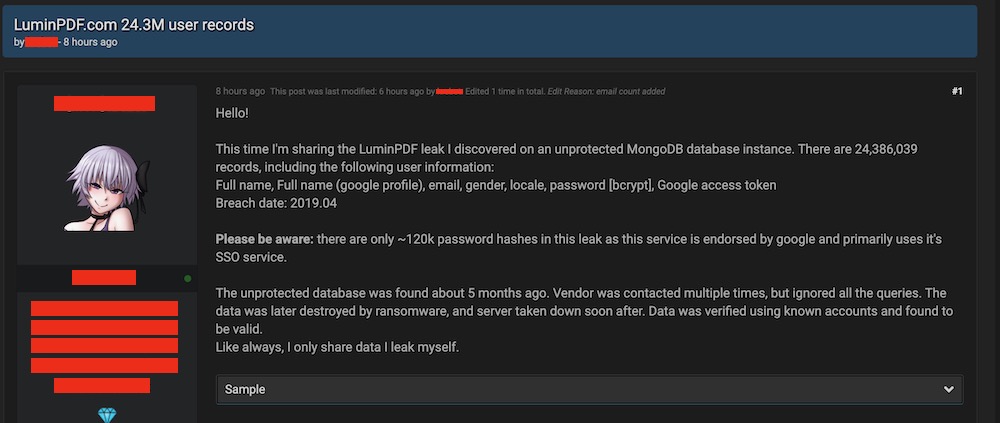
Ignoring a breach disclosure can have ugly consequences. Case in point: Lumin PDF, a PDF editing tool, which saw data for much of its user base - about 24.3 million - published in an online forum late Monday.
See Also: Overcoming Unstructured Data Security and Privacy Choke Points
Lumin PDF, a product of NitroLabs of New Zealand, is free PDF editing tool that offers tiered subscriptions for more advanced features and storage.
The published data includes users' full names, Google profiles, email addresses, locales and in some cases, Google access tokens and hashed passwords.
The person who says he found the data, who asked not to be named, tells Information Security Media Group that his team found a MongoDB database belonging to Lumin PDF accessible online around mid-April. He says he reached out to NitroLabs, including its founder and CEO Max Ferguson, on his personal email, but did not receive a response.
Data Dump
Efforts to reach Ferguson, a native New Zealander who’s LinkedIn profile says he is a research assistant at Stanford University in California, and NitroLabs, were unsuccessful.
A few weeks after discovering the database, the person who discovers it says, it was hit with ransomware. Ransomware attackers often scan the internet for MongoDB instances that have been left open and require no authentication to access. The database was taken down some time after that happened, the person wrote in his post on the hacker forum (see MongoDB Ransomware Compromises Double in a Day).
Since Lumin PDF did not respond, the person says he decided to publicly release it on a well-known forum for publishing data leaks. Security researchers sometimes choose this route in frustration after trying to raise attention.
“The decision to release it was hard, but we had evidence that it was already leaked multiple times and there were third parties that may be already using the data and since Lumin did not respond, we decided to release it this way,” the person says. “We do security research professionally and usually disclose everything responsibly, but this time it was the ignorance that motivated [us] to do this.”
Access Token Leak
A sensitive aspect of the breach is the leak of Google account access tokens. Lumin PDF allows users to use either their Google or Dropbox credentials to sign into the service. That allows Lumin to have access to, for example, a person’s Google Drive storage and email.
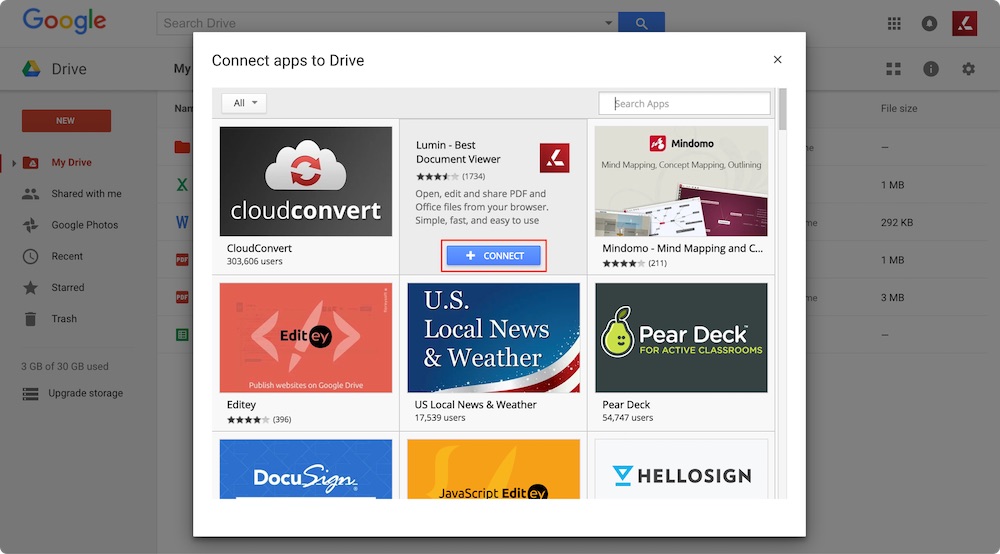
Capturing those access tokens is valuable to cybercriminals, because it could provide access to someone’s Dropbox or Google Drive account. One of the comments posted following the leak on the hacker forum says: “Data looks good and its not 'that' old. So you might be able to reuse some of these Google tokens since they usually don’t expire that quickly.”
The person who found the data says he held off posting it sooner due to the access tokens, saying that the four-month delay should have allowed most of the tokens to expire.
Because most Lumin PDF users signed in using Google or Dropbox credentials, there were less than 120,000 password hashes in the database. Those passwords were hashed with bcrypt, which is considered a strong hashing algorithm. Bcrypt is more resistant to password cracking because it takes much longer to generate possible matching hashes.
“Bcrypt is hard to crack,” says the person who found the data. “We weren’t able to crack a single hash on the database.”
15.4 Unique Email Addresses
Many email addresses in the leak appear to have never been leaked before, says Troy Hunt, a data breach expert who runs the Have I Been Pwned breach notification site. Hunt says his analysis shows that of 24.3 million email addresses, 15.4 million are unique.
Hunt compares new breaches against his trove of data breaches to see if newly leaked email addresses match with those from previous breaches. Now that the Lumin PDF data is public, Hunt plans to add it to Have I been Pwned.
The larger question, he says, is why Lumin PDF never responded to the original breach notification, which would have helped alert users earlier and may have prevented data from being publicly released. The fact that the service kept running after the MongoDB was frozen by ransomware indicates the company likely knew it had been compromised, he says.
“For me personally, the most interesting thing about this is the huge volume of data that’s out and absolutely nothing has happened,” Hunt says.
Although ISMG couldn’t reach Ferguson, he did respond to a query from ZDNet. Ferguson told ZDNet that all of the Google tokens were expired at the time of the breach. He says that Lumin PDF planned to disclose of the breach in a blog post on Tuesday. As of Wednesday morning U.S. Eastern time, Lumin PDF's site did not have a notification.
Hunt says that’s an indication of just how broken the breach notification process is.
“Every single one of those people [in the breach] want to know,” Hunt says. “They will want to be told when their data is exposed in this fashion.”